AI project Port3 cross-chain bridge was breached: hackers printed 1 billion coins and sold them, and the currency price crashed by 80%
Port3 Network cross-chain bridge was illegally minted by hackers, with 1 billion coins plunging 82% in one hour, once again exposing the security concerns of DeFi cross-chain bridges.
(Preliminary summary: Balancer gave the hackers an "ultimatum" of 96 hours to pay back the money: otherwise they will use all means to find you)
(Background supplement: Arthur Hayes: Bitcoin is about to hit bottom, but don't be in a hurry! You have to wait for the US stock market to collapse again before "printing money")
1430 Update》Port3 Network After the hack, the official decided to issue new tokens and contracts to restart the ecosystem, and $PORT3 returned to zero
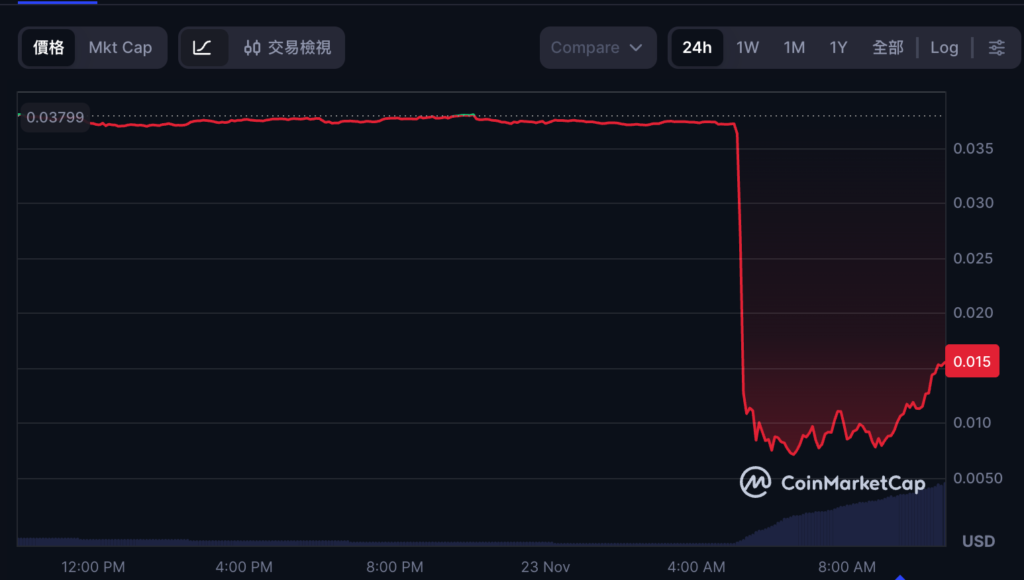
At around five o'clock in the morning today (23rd), the decentralized AI data network Port3 Network was shocked to report a major information security incident. Hackers targeted BridgeIn, its cross-chain bridge component, and illegally minted 1 billion PORT3 tokens. The selling pressure instantly drove the price from $0.037 to as low as $0.0066, a drop of as much as 82% in just one hour.
Attack details and fund flow
It is understood that hackers used BridgeIn A smart contract vulnerability bypassed issuance restrictions and minted PORT3 out of thin air, with a market value of approximately $13 million. According to on-chain data, after the attacker sold 162.75 million tokens to cash out, the project team urgently removed the liquidity pool to block further cash out.
Subsequently, the hackers directly destroyed the remaining 837 million tokens that could not be processed. Port3 official announcement on the community:
"We have temporarily removed liquidity and are fully investigating, and will try to communicate with the hackers."
Market Impact and Follow-up Warning
Although the price of PORT3 has rebounded to US$0.015 after the incident, liquidity is weak and confidence has plummeted. This incident reminds investors that cross-chain bridge permission management and auditing are still the most vulnerable links in the Web3 ecosystem.
Faced with immature contract mechanisms, you should pay attention to the security history of the chain where the funds are located and the bridging tool to avoid irreversible losses caused by a single vulnerability. At this stage, investors should observe the project party’s subsequent compensation and security upgrade plans, and do not rush to buy the bottom because the price has dropped.